An active attack involves changing the information in some way by conducting some process on the information. For example,
- Modifying the information in an unauthorized manner.
- Initiating unintended or unauthorized transmission of information.
- Alteration of authentication data such as originator name or timestamp associated with information
- Unauthorized deletion of data.
- Denial of access to information for legitimate users (denial of service).
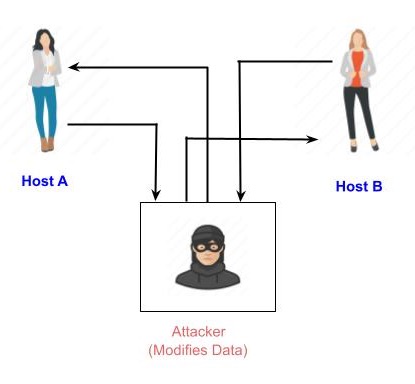
Cryptography provides many tools and techniques for implementing cryptosystems capable of preventing most of the attacks described above.
Assumptions of Attacker
Let us see the prevailing environment around cryptosystems followed by the types of attacks employed to break these systems −
Environment around Cryptosystem
While considering possible attacks on the cryptosystem, it is necessary to know the cryptosystems environment. The attacker’s assumptions and knowledge about the environment decides his capabilities.
In cryptography, the following three assumptions are made about the security environment and attacker’s capabilities.
Leave a Reply